|
|

|
AD: Upgrade ArcaOS to NeoWPS level
- Install original PNG icons drawed by designer, specialized at OS/2 adornation.
- Install eSchemes 2019 to change colors and buttons on desktop.
|
TITLE: NetDrive Cipher plugin
DATE: 2001-09-04 00:21:20
AUTHOR: Andrei A. Porodko
Introduction. One day I realised that I need to hide some of my data from strangers. That doesn't mean I have an access to X-Files, but everybody has something "for his eyes only". That's getting more important in case have your own business. Nobody yet has disabled the market competition. I've searched the Hobbes archive and other Internet sites for an application that would allow me to encrypt my data. Most of found links are dead, some developers had moved to Windows or Linux. Nevertheless I've found some useful products. Unfortunately they use old encryption algorithms such as DES. I thought that there must be an application with stronger encryption, and I was right, because there was the Cipher plugin for NetDrive for OS/2.
What is the Cipher plugin ? Cipher plugin is a dynamic loadable library that used by NetDrive for OS/2 for transparent data encryption/decryption. Like all NetDrive plugins the Cipher is a part of the IFS (installable file system) called NDFS (NetDrive File System). It works imperceptibly and quietly, but provides strong encryption and as a result good privacy for your data.
What can and can't the Cipher plugin do ? Cipher plugin allows you to create protected disks and folders within NetDrive File System and to use the data stored on those disks and folders as if it was ordinary data on an ordinary OS/2 storage device. Cipher protects selected part of files on your disk or diskette, in addition Cipher hides the file date/time and size. Cipher can't encrypt neither your e-mail messages sending via cables nor any traffic in wires. For those purposes you can use other products, for example PGP for e-mail, IBM firewall for private networks.
Cipher plugin can use different cryptography methods (algorithms). At the moment the following methods are ready to use:
- Blowfish, key length 1-56 bytes;
- Cast 256, 1-32 bytes;
- GOST (this is the standard method in Russian), 32 bytes;
- Loki97, 1-32 bytes;
- Mars, 1-160 bytes;
- RC6, 1-255 bytes;
- Rijndael, 1-32 bytes;
- Safer Plus, 1-32 bytes;
- Serpent, 4, 8, 12 ... 32 bytes;
- Tripple Des, 24 bytes;
- Twofish, with 16, 24, 32 bytes keys long.
How to install ? Plugin installations is very easy with the NetDrive 2.0 version. Cipher plugin distributed in archive ndpcphr.zip. You have to unzip it into an empty directory. Then run instlpl.cmd from the directory. You do not have to reboot the system.
How to work with Cipher plugin ? Create a directory somewhere on your hard disk or diskette (of course it can be a root directory). Inside this directory you will store crypted data. Decide which crypt-algorithm is preferable for your aims and what will be the key length. We don't provide any information about that, because data protection is rather complicated field and it is better to find good expert. You can read about algorithms those used in the plugin at the sources listed in Bibliography.
As every NetDrive resource, Cipher has to be mounted before accessing. Note. There is a sample sequence of commands for mounting Cipher resource :
nd attach u:
nd createmp u:\Secret
nd mount cipher u:\Secret ;name=blowfish.dll;root=D:\Secret;round=1;key=C:\NDFS\key w
At first you create a new NetDrive drive letter.
Second line creates a mount point for mounting Cipher resource.
Third line mounts Cipher resource into the created mount point.
There are four parameters for the Cipher plugin :
name - name of the dynamic link library that implements encryption method you selected, all those libraries are in ndplugs\cipher sub-directory. If you use different cipher or cipher library is placed in another directory, you should enter full path to this library. There is no default value for this parameter.
root - the name of the directory we've created to save protected data to. There is no default value for this parameter.
round - number of encoding iterations (default - 1). Note : more iterations provides stronger encryption but less speed.
key - full name for the file where your key (key is a sequence of hexadecimal digits) is saved. There is no default value for this parameter.
Note. Cipher plugin needs your key only during mounting, after that you can (have to ?) remove the diskette with a key and put it in safe place. NOTE. YOU HAVE TO KEEP YOUR KEYS IN THE SAFE PLACE !!! Don't spread keys around your disks, write them into diskette, make a copy and keep both copies separated somewhere physically protected.
You can also use NetDrive Control Panel to mount Cipher resource. Look at the screen shot below :
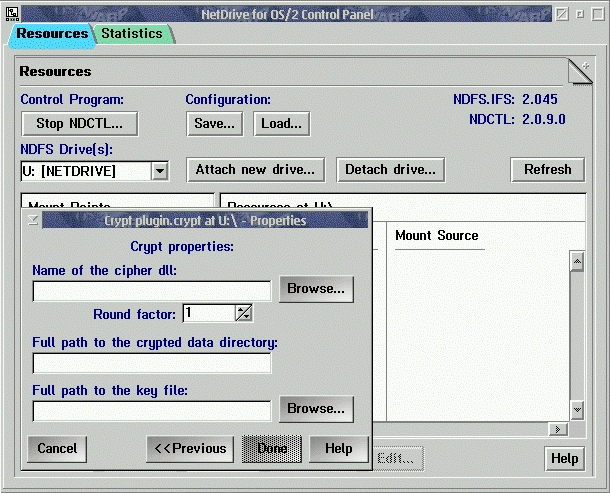
You attach new drive and create mount point by pressing a few buttons. Than you select the created mount point and press 'Mount' button. Choose 'cipher' type form the list and to fill in the form with values described earlier. In the Control Panel you can save all your adjustments and then restore whenever you need.
After mounting, Cipher resource is ready to use. All files copied or created in the mount point will be encrypted and saved in cipher. Plugin doesn't keep your key in memory, so that fact decreases the probability of its unfolding. To close the access to your encrypted data you should unmount Cipher:
nd unmount u:\Secret 0
This action could be performed on the Control Panel by selecting the Cipher resource and pressing "Unmount" button.
I would like to offer more secure and convenient way on my opinion - install one of hot-key popup managers and assign unmount action to one of the hot-keys. I installed "Keyboard Plus" taken from Hobbes archive. And now Ctrl-Alt-F12 closes access to my private data.
There is another important thing you should know - key generation. Utility for key generation cryptkey.exe is included in the plugin distribution package and is placed into the NetDrive directory (usually C:\NDFS). Cyptkey.exe is designed as a command line utility in an expectation of a very seldom usage. Key generator has only one parameters, a number - length for generated key in bits (not bytes !) of the key to be generated.
For example I need a key with a length 128 bit (16 bytes long) :
C:\NDFS>cryptkey.exe 128
0fa5fd48b78ca2bc8816001c36c4ea804dce102860491fd4a604b12f83
c357f3200000008aac41000b39140a1d08d107ffff0300800000009894
04003f39020002000aad628e2d031ca1fddc09c83fe1e28a9d8d0b530b
2401e63fd4524484d273f1d726a8828f234b07125544a588d09c263078
e3aa352f78b0be36994d0de0
As you can see, program writes key on screen. Let's modify a bit our command line and redirect output into a file on diskette :
C:\NDFS>cryptkey.exe 128 >A:\mykey
Perhaps you'll find more useful the Rexx command file cipherkey.cmd which is also included in the plugin distribution package. It works directly with cipher names, keys lengths in bytes and writes the key immediately into the file.
D:\NDFS>cipherkey.cmd
Wrong arguments
Usage:cipherkey.cmd
Known ciphers are:
blowfish - valid key lengths are 1 - 56 bytes
cast256 - valid key lengths are 1 - 32 bytes
gost - valid key length is 32 bytes
loki97 - valid key lengths are 1 - 32 bytes
gost - valid key length is 32 bytes
mars - valid key length are 1 - 160 bytes
rc6 - valid key length are 1 - 255 bytes
rijndael - valid key length are 1 - 32 bytes
serpent - valid key length are 4 - 32 bytes by 4 bytes
tripdes - valid key length is 24 bytes
twofish - valid key length is 16, 24, 32 bytes
Note. Keys are random numbers. It's impossible to restore key if you've lost it. Key generator never produces two equal keys.
Cipher plugin has one side effect - if you mount FAT disk or diskette as a secure resource you will be able to save files and directories with long names there despite they aren't supported by such file systems.
In conclusion I want to illustrate the Cipher plugin usage. Imagine a firm with several computers. Firm's staff have to keep an electronic archive and from time to time have to exchange data on removable media (for example ZIP-diskette). They've got NetDrive and Cipher plugin installed. All removable media on those computers mounted through Cipher plugin. In such conditions if any diskette would be stolen, burglar never read even a word from your data.
If you have bug report or suggestions, you are welcome.
Bibliography, used algorithms references :
http://cnscenter.future.co.kr/crypto/algorithm/block.html
http://csrc.nist.gov/encryption/aes/round1/round1.htm#algorithms
Cipher plugin (C) 2001 Nickk
NetDrive (C) 2000-2001 Blueprint Software Works. http://www.blueprintsoftware.com/netdrive
Documentation copyright (C) 2001 Andrei A. Porodko
Comments: Axel Hagedorn 
2001-11-19 23:32:11 | The key generator takes a "byte"-parameter - not a "bit-parameter!
The given example for 128 bit actually shows a 128 byte key
(256 hex-numbers with each one representing 4 bit). |
Comment this article.
|





